Configure input filtering
Preamble
Filtering functions allows disabling access to the site to some of the requests made. This can be done either depending on the content of the request, on who performs the request or on the requested URL itself.
Variable filtering
As sh404SEF will normally decodes any incoming request to your web site, it's ideally placed to perfom some simple checks on the nature of this request. After turning a SEF URL into its non-sef counterpart that Joomla! can use, but before returning control to Joomla!, sh404SEF can make sure some predefined variables contains values that are of a given type.
This provides an additional level of filtering, in case some extensions don't perform it properly. But a major gain is also to stop those attacks as early as possible and thus preserve serve resource.
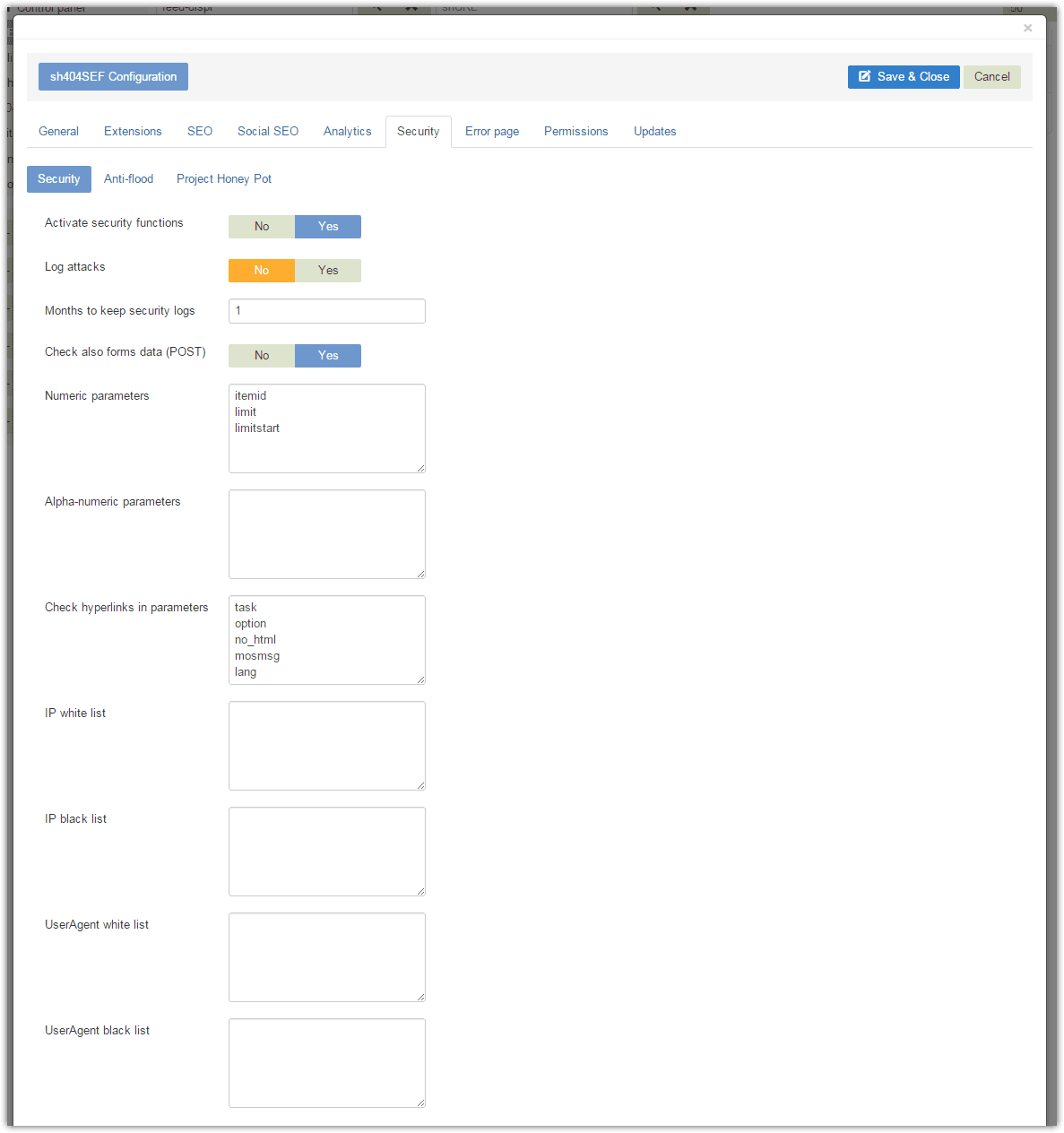
Secured variables can be of two types: Numeric or Alpha-numeric.
Numeric: the controlled variable passed in the request can only be an integer number. Any request with listed variables not numeric will be denied.Alpha-numeric: the controlled variable can consist only of digits (0-0) and letters (a-z). Other requests will be denied.
By default, sh404SEF is setup to perform those tests on common Joomla! variables themselves.
POST Data filtering
The same controls and a few more can be enabled on POST data. POST data is when you fill out a form and the data in that form is sent by your browser to your Joomla site. Enabling security checks on the posted forms content may result in false positives, ie legit content being blocked such as script tags in front-end edited content for instance. Therefore you should disable this fature if you experience such false positives.
IP filtering
Instead of looking at what the request is, sh404SEF can also block or allow a request based on who is making it. You can white-list or black-list some IP addresses by adding them to the corresponding input field (one per line):
- IP addresses listed in the
white-listfield will be allowed. IP addresses listed in theblack-listinput field will be denied access. - If an address is in both field, access will be denied
- IP addresses can use
*as wild card characters.192.168.1.*means that any IP address starting with 192.168.1 will be granted/denied access
User-agent filtering
User agent filtering works exactly the same way as IP address filtering, except that the provided strings will be checked agains the requester user agent string.
- User agent check is done after IP address check, meaning that even if a user agent string is white-listed, it'll be rejected if it comes from a black-listed IP address. On the opposite, if an IP address is white-listed, that's not enough to pass if the requester user-agent string is black-listed.
- It's enough to specify a part of the user agent string to have a match. Entering "explorer" in the black-list box will deny access to requester with user agent strings such as "Internet Explorer", "Theexplorer", "Some EXPLORER".