URL blocking configuration
Using the URL blocking feature, you can stop some obviously inappropriate requests very quickly to avoid wasting precious server resources on them. Typically, such requests will be well-known bots requests to your site trying to attack it or just identify it. The most common ones are requests directed at WordPress (!) sites. Malicious attackers simply sends them to all sites they can find, whether WordPress or not. This can result in added load on your server and reduced speed for your legitimate visitors.
sh404SEF comes with rules to block those common WordPress-targeted requests and you can add your own rules to block other URLs, specific to your use case. Here is the configuration screen.
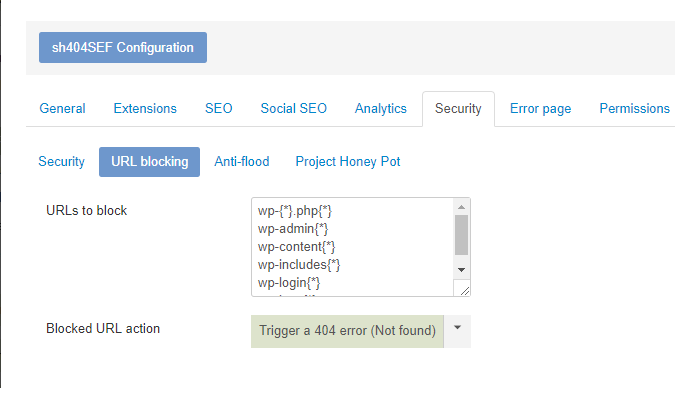
URLs to block
You can enter one rule per line in that input field. Do not include the domain name or a leading slash. You can also include wildcard characters such as {*} and {?} to represent, respectively: any number of any characters, or any single character.
Here are a few examples:
some/url.htmlwill block requests to https://example.com/some/url.html, and that URL only.
some/url{*}will block requests to
https://example.com/some/urlhttps://example.com/some/url/https://example.com/some/url.htmlhttps://example.com/some/url.phphttps://example.com/some/url/and-many-more
and all requests to URLs that starts with https://example.com/some/url
The default rules included with sh404SEF are:
wp-{*}.php{*}
wp-admin{*}
wp-content{*}
wp-includes{*}
wp-login{*}
wp-json{*}Action to take
When a request matches one of the above rules, you can select to:
- do nothing (during development and testing for instance)
- Trigger a 404 error (page not found)
- Trigger a 403 error (forbidden request)
The default is to trigger a 404 error page.