Hey there,
Frontend editor trying to embed a javscript file with script tags result into a Forbidden Access error for them.
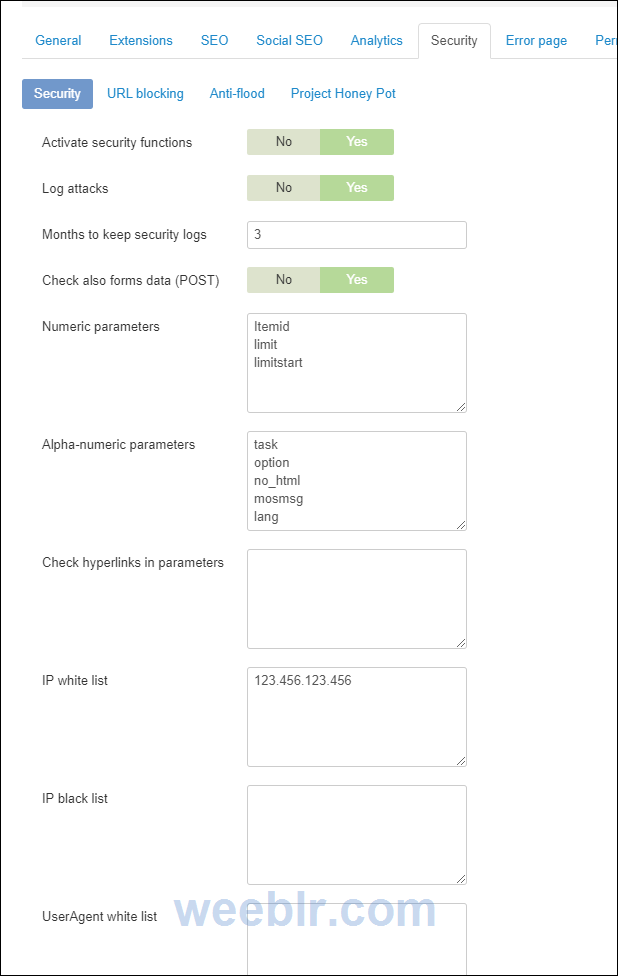
Turns out this is due to sh404sef security features being enabled.
This only happens for lower-ACL users. Me as an administrator can add scripts from the frontend just fine, but authors or editors can't.
Is there any way around this?
Thanks!
Frontend editor trying to embed a javscript file with script tags result into a Forbidden Access error for them.
Turns out this is due to sh404sef security features being enabled.
This only happens for lower-ACL users. Me as an administrator can add scripts from the frontend just fine, but authors or editors can't.
Is there any way around this?
Thanks!